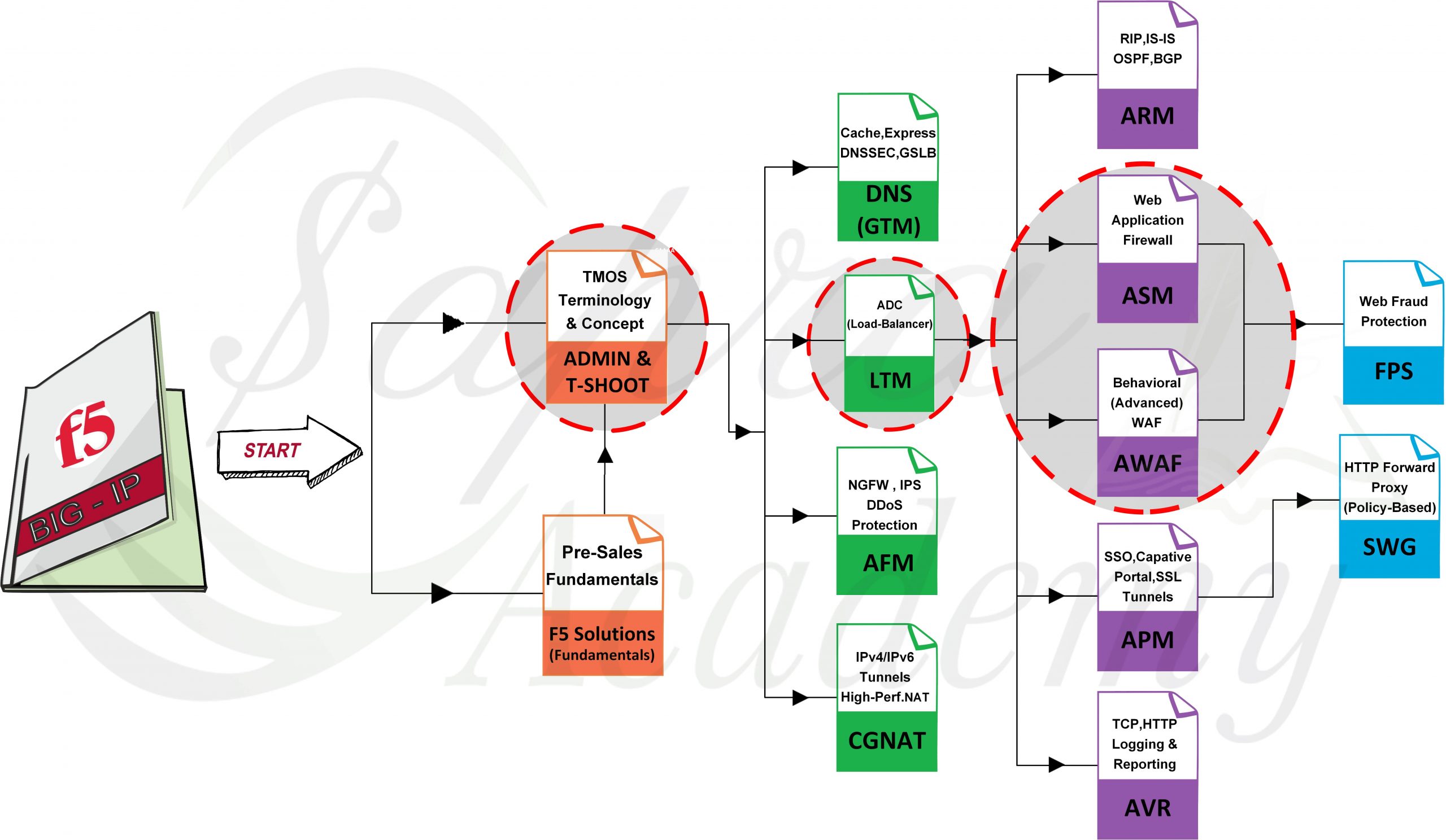
این دوره بصورت فشرده شامل سرفصل دوره های F5 BIG-IP Administration & Troubleshooting و F5 BIG-IP LTM Administration و F5 BIG-IP ASM/AWAF Administration می باشد. قطعا جهت آشنایی حرفه ای تر و درک عمیق تر سرفصل های این دوره، گذراندن دوره Advanced + Workshop نیز پیشنهاد می شود.
پیش نیاز دوره:
- Network+
- Security+
- HTTP Protocol Security
- CCNP R&S
مدت زمان دوره: 120 ساعت
مدرس دوره: مهندس پرهام امام جمعه
سرفصل دوره:
F5 BIG-IP Administration and Troubleshooting
- Application Delivery Controller – Deployment Method
- BIG-IP Terminology and Concepts
- VLAN, Self-IP, Floating-IP and Access Management
- Pool, Pool Member and Node
- Configuration of Different Pool Monitors
- NAT, SNAT and DNAT configuration
- Full-proxy Architecture with NAT Operation
- Configuration of Important Traffic Profiles
- HA (High Availability) Configuration and Fail-safe
- Hardware Diagnostics
- TMSH Commands for BIG-IP Administration
- TCPDUMP Command for Traffic Capturing
- AOM (Always-On Management)
- Leveraging iHealth to Check Functional Status of Device
- Software and Configuration Maintenance
- Creating Backup Files and Restoring Backup
- Administrative Partitions
- Different User Roles
- F5 BIG-IP Maintenance
- External APIs, Programming or Automation Interfaces
- F5 Support Resources and Tools
- APPENDIX: TMOS v12.0, v13.0, v14.0, v15.0 (New Features)
F5 BIG-IP LTM Administration
- Introduction to Load-balancers
- Load-balancers and Deployment Methods
- Load-balancer Terminology and Concepts
- VLAN, Self-IP, Floating-IP and Access Management
- Working With Administrative Partitions and Route Domains (VRFs)
- Configuration Local Traffic Policies for HTTP Traffic Management
- Intelligent Traffic Management via iRule Scripts
- Load-balancing Methods, Applications and Configuration
- VS (Virtual Server) Types, Applications and Configuration
- Advanced HA (High Availability) Configuration
F5 BIG-IP ASM/AWAF Administration
- Web Application Security
- OWASP- Top 10 Application Security Risks
- OWASP Automated Threat Events
- WEB Application Vulnerability Reports (2020)
- WAF Deployment Methods
- Introduction to F5-ASM
- F5 AWAF (Advanced WAF)
- Application Security Policies
- Application Security Policy Entities
- Attack Signatures Management
- Fine-tuning of Security Policies
- Additional Application Security Protections
- DoS Attacks Detection and Mitigation
- Brute Force Attacks Detection and Mitigation
- Web Scraping Attacks Detection and Mitigation
- Using iRule Scripts with ASM/AWAF
- HA (High Availability) Configuration
- Important User Accounts
- Checking Health, Logs and Reports